Table of contents
Introduction:
DevSecOps represents a methodology within software development that prioritizes the integration of security measures across the entire lifecycle of software development. This approach, encapsulated in the acronym DevSecOps, emphasizes the seamless inclusion of security considerations alongside development, operations, and other pertinent phases. The primary goal of DevSecOps is to enforce security measures consistently and comprehensively throughout various stages of software development, encompassing planning, development, testing, release, delivery, deployment, operation, and monitoring.
Project Phases Overview:
Our project is structured into two distinct phases:
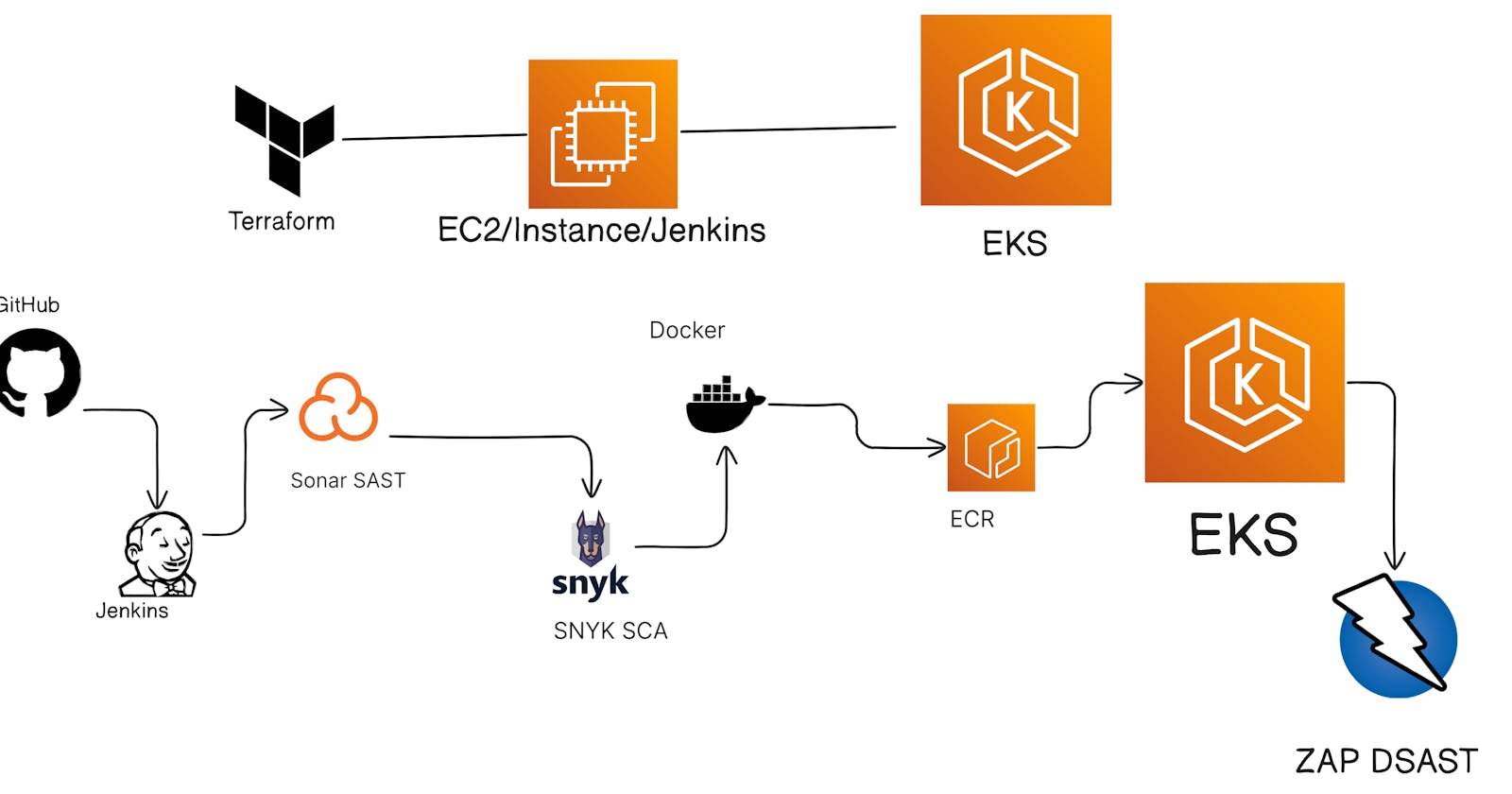
Infrastructure as Code (IAC) - Leveraging Terraform
Continuous Integration and Continuous Deployment (CICD) Pipeline
Highlighted Tools:
For the effective execution of our project, we're utilizing a suite of tools tailored to each phase:
Terraform for Infrastructure as Code
GitHub for version control and collaboration
Jenkins as the Continuous Integration (CI) tool
Sonarcloud for Static Application Security Testing (SAST)
Snyk for Software Composition Analysis (SCA)
Docker for containerization and build processes
Amazon Elastic Container Registry (ECR) for managing artifacts
Amazon Elastic Kubernetes Service (EKS) for container orchestration and deployment
ZAP for Dynamic Application Security Testing (DAST)
Accessing the Infrastructure as Code (IAC) Repository:
Phase 1 : Infrastructure as Code (IAC) - Leveraging Terraform
The code related to the Infrastructure as Code phase can be found in the following repository: GitHub Repository Link
Setting up the Environment: Before diving into the Terraform code, ensure you have Terraform installed on your local machine. Additionally, you'll need an AWS account and appropriate credentials configured on your system.
Understanding the Terraform Configuration: Let's break down the Terraform configuration provided:
Terraform Block:
- Specifies the required Terraform version.
Provider Block:
- Configures the AWS provider with the specified region.
Variables:
- Defines variables for AWS region, VPC ID, and key name.
AWS Security Group Resource:
- Creates a security group allowing traffic on port 8081 for Jenkins and SSH access on port 22.
AWS AMI Data Source:
- Retrieves the latest Amazon Linux AMI matching specific criteria.
AWS IAM Role and Instance Profile:
- Creates an IAM role and instance profile for EC2 instances.
AWS IAM Role Policy:
- Attaches a policy allowing all actions on all resources to the IAM role.
AWS Instance Resource:
- Launches an EC2 instance using the specified AMI, instance type, key name, security group, and user data script.
Provisioning the Jenkins Server: To provision the Jenkins server, follow these steps:
Clone the Terraform configuration provided.
Modify the variables.tf file to specify your AWS region, VPC ID, and key name.
Create an install_jenkins.sh script with the necessary commands to install Jenkins.
Run terraform init to initialize the Terraform environment.
Run terraform plan to preview the changes.
Run terraform apply to provision the resources on AWS.
Refer Readme Section in the repository
EKS- Cluster Creation :
Once is Terraform is setup is complete Run below code to create a EKS manged cluster using below command.
eksctl create cluster --name kubernetes-cluster --version 1.23 --region us-east-2 --nodegroup-name linux-nodes --node-type t2.xlarge --nodes 2
"Next, we will delve into the Phase 2 project in our upcoming blog post, offering a glimpse into what lies ahead."
Jenkins Pipeline Overview :

Feel free to contact me via LinkedIn if you encounter any issues or need support.